New Outlook: The End of Email Privacy?
Logs verify that the new Outlook client transmits raw IMAP passwords to Microsoft servers.

Microsoft’s latest iteration of its email client, "New Outlook," has fundamentally shifted its architecture from a local application to a web-based service wrapper, resulting in alarming implications for data privacy and security. The following analysis details a technical experiment demonstrating how Microsoft systematically captures user credentials and mirrors data from third-party mail servers, effectively performing a Man-in-the-Middle (MitM) operation on unsuspecting users.

I needed to test this myself.
The Experimental Setup
To verify the behavior of the "New Outlook" client (and its mobile counterparts), a strictly isolated "clean room" environment is required to eliminate background noise and potential cross-contamination from existing accounts.
The test environment consists of a freshly provisioned Virtual Private Server (VPS) hosting a standard Linux mail stack. A Debian-based system serves as the foundation, running Postfix for SMTP and Dovecot for IMAP services. This server is configured with a valid SSL/TLS certificate (via Let's Encrypt) to ensure encrypted transport, simulating a typical professional self-hosted email environment. Crucially, this server has never communicated with the outside world prior to the test.
On the client side, a pristine virtual machine running Windows 11 is utilized. The network traffic is monitored both at the virtualization gateway and on the mail server itself using tools like tcpdump and standard system logs.
The Anomaly in the Logs
The critical moment occurs immediately after configuring a generic IMAP account (e.g., michael.test@testmail.meister-security.de) within the New Outlook client. The user enters their hostname, username, and password into the application running on their local Windows machine.
Under standard protocol behavior (RFC 3501), one would expect the IMAP connection to originate from the client's IP address (e.g., the residential ISP or office network). However, an inspection of the Dovecot authentication logs reveals a completely different reality.
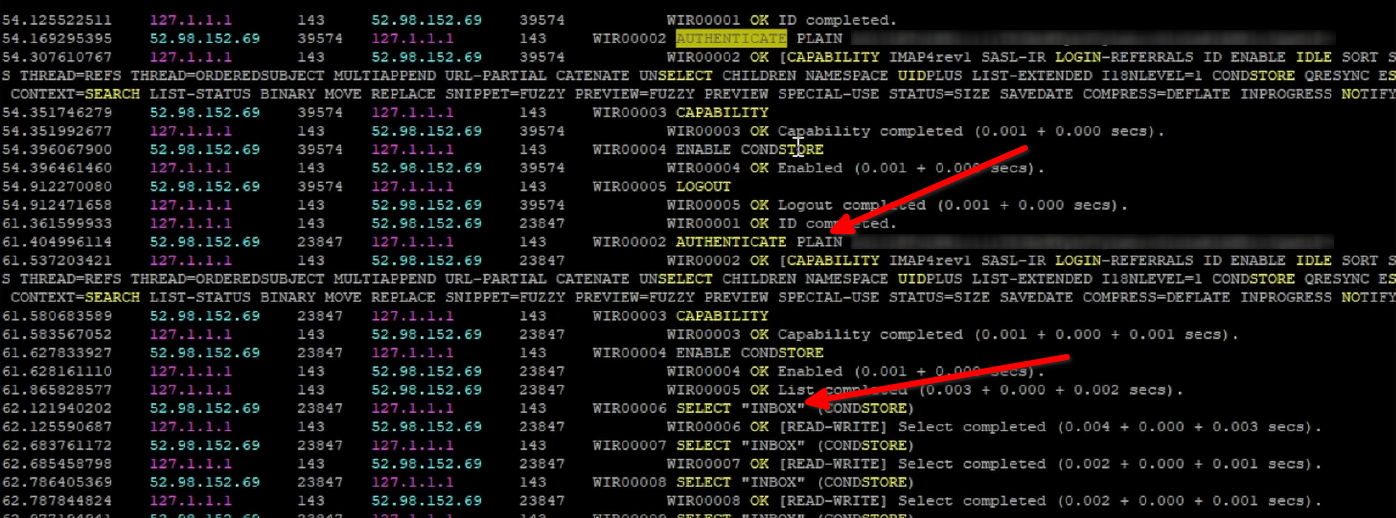
A simple whois lookup on the Remote IP (rip) addresses 52.98.152.69 and 52.96.0.14 confirms the suspicion:
$ whois 52.98.152.69
NetRange: 52.84.0.0 - 52.95.255.255
CIDR: 52.84.0.0/14
OrgName: Microsoft Corporation
OrgId: MSFT
Address: One Microsoft Way
City: Redmond
The connection is not established by the local Outlook client. Instead, the credentials entered locally were transmitted to Microsoft's cloud infrastructure (specifically Azure servers, often located in Dublin or the US), which then initiated the login attempt to the private mail server.
Data Exfiltration and Synchronization
The implications of the log entries above are severe. For the connection from Microsoft's servers to succeed, Microsoft must possess the plaintext password of the user's email account.
To prove that this is a persistent cloud synchronization rather than a one-time tunnel, the local Windows client is disconnected from the internet entirely. Despite the user's machine being offline, the mail server logs continue to show periodic login attempts and synchronization commands (fetching folder lists, downloading emails) originating from Microsoft's IP range.
This confirms that Microsoft is effectively cloning the external mailbox onto their own servers ("Exchange Online" infrastructure). The local Outlook application is merely a remote view of this Microsoft-hosted shadow copy.
The Privacy Implications for Gmail
While the test above utilized a standard IMAP account (requiring raw password storage), the architecture implies similar data sovereignty violations for providers like Gmail. When adding a Gmail account, Microsoft now posesses username and password for your Google-Account. And that's not only for Mail! That way Microsoft gains persistent, server-side access to the user's entire digital life across competing ecosystems. This data is suddenly subject to Microsoft's terms of service, regardless of the original provider's privacy policy.
Conclusion
The analysis demonstrates that the "New Outlook" acts as a data vacuum, intercepting credentials for non-Microsoft accounts and transferring them to the Microsoft Cloud without explicit, transparent warning about the architectural shift. By acting as a Man-in-the-Middle, Microsoft bypasses the expected end-to-end privacy of a standalone email client, effectively treating private, self-hosted, or third-party data as its own.

